
The Chinese hacking group Apt41 uses a new malware named “ Durprogress ” which operates the Google calendar for command and control operations (C2), hiding a malicious activity behind a confidence cloud service.
The campaign was discovered by Google threat intelligence groupwhich has identified and dismantled and dismantled the infrastructure of the Google calendar and the workspace controlled by the attacker and introduced targeted measures to prevent such abuses in the future.
The use of the Google calendar as a C2 mechanism is not a new technique, and Veracode recently reported About a malicious package in the noded package manager index (NPM) according to a similar tactic.
In addition, Apt41 is known to abuse Google services before, such as the use of Google Sheets and Google Drive in a Voldemort malware campaign in April 2023.
Source: Google
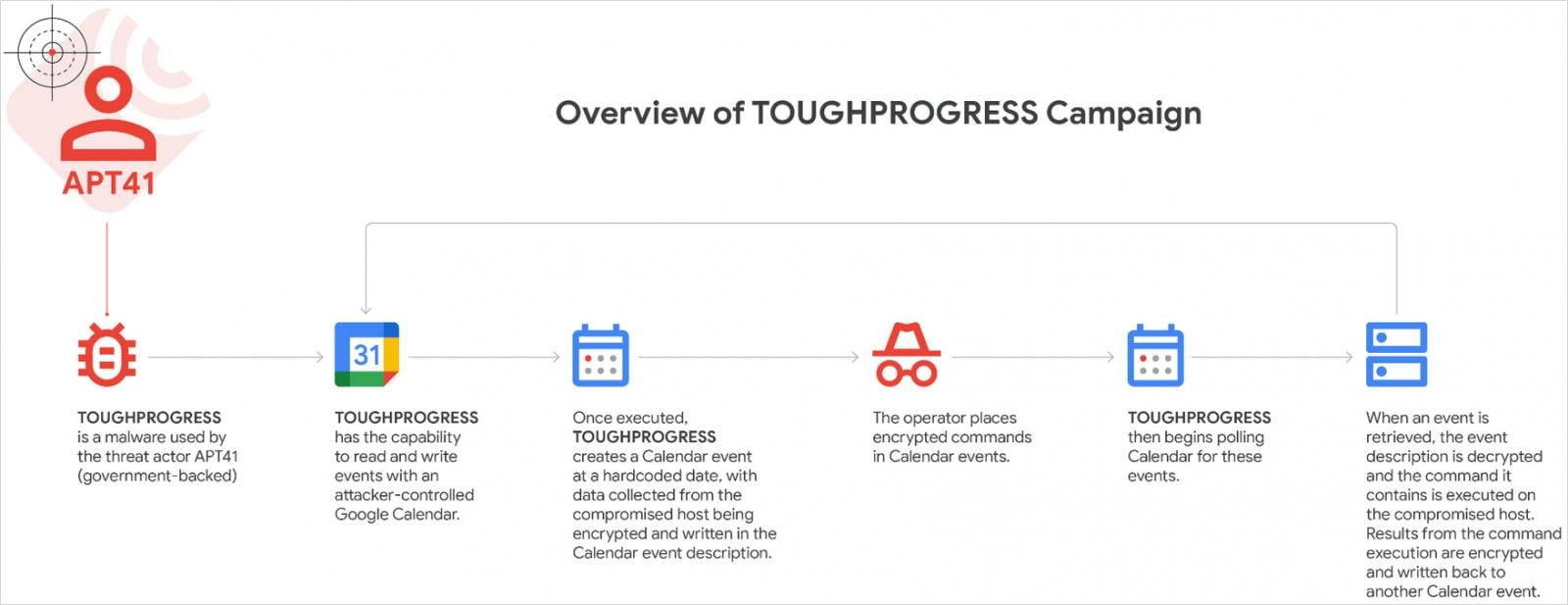
APT41 Attack flow
The attack begins with a malicious email sent to the targets, connecting to a ZIP archive hosted on a website of the previously compromised government.
The archive contains a Windows LNK file, pretending to be a PDF document, a masked main payload as a JPG image file and a DLL file used for the decryption and launch of the payload, also camouflaged as an image file.
“The files” 6.jpg “and” 7.jpg “are false images. The first file is actually an encrypted payload and is decrypted by the second file, which is a DLL file launched when the target clicks on the NNK”, explains Google.
The DLL is “Plusdrop”, a component that deciphers and performs the next step, “moreject”, entirely in memory.
Then, Plus injects a processes on the legitimate Windows process “svhost.exe” and injects the last “Durprogress” step.
The malicious software connects to a climbs ending google calendar termination and the dates of specific events with Apt41 controls add the field of description of hidden events.
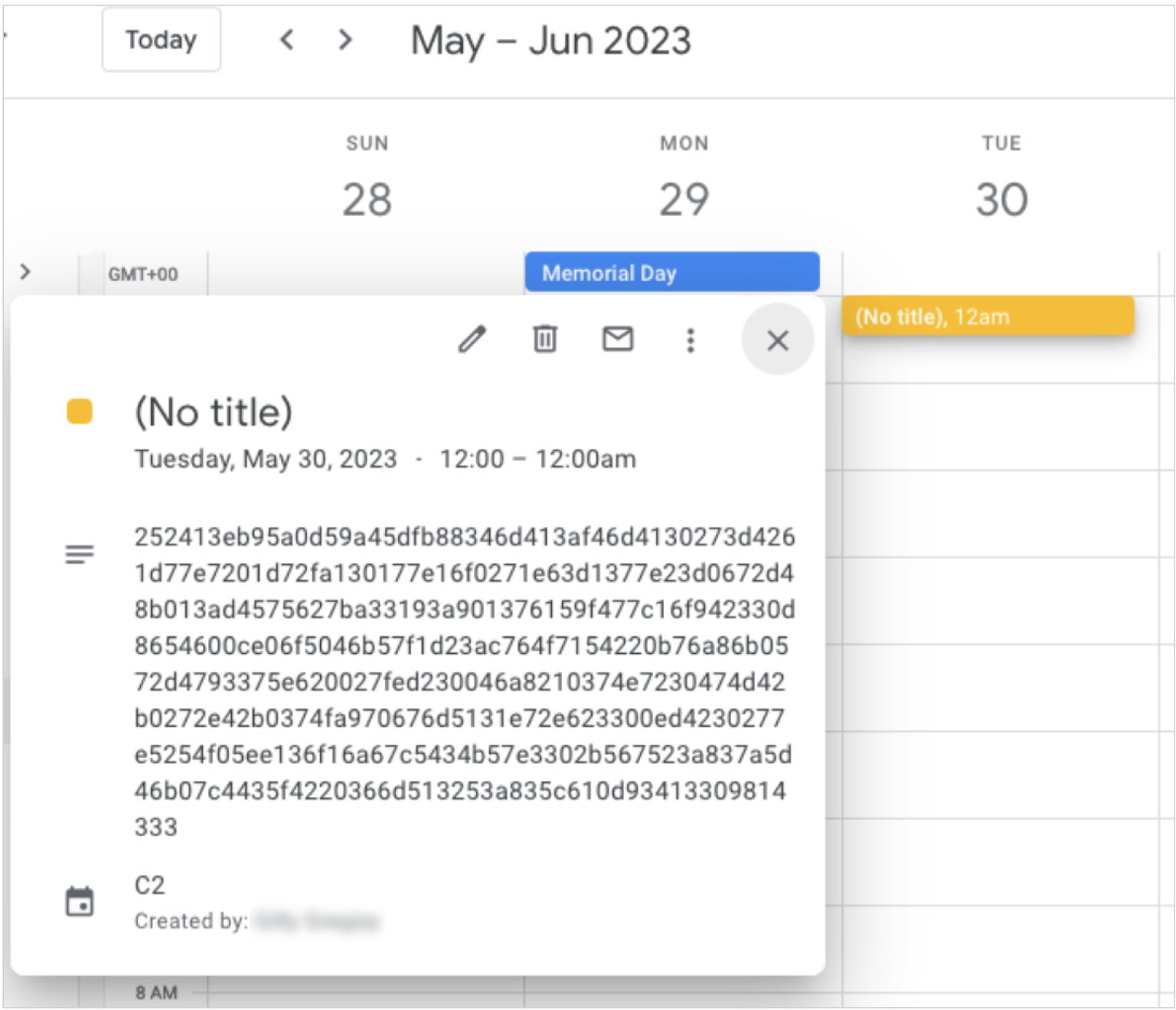
Source: Google
After having executed them, ToughProgress returns the results in new calendar events so that the attacker can adjust his next steps accordingly.
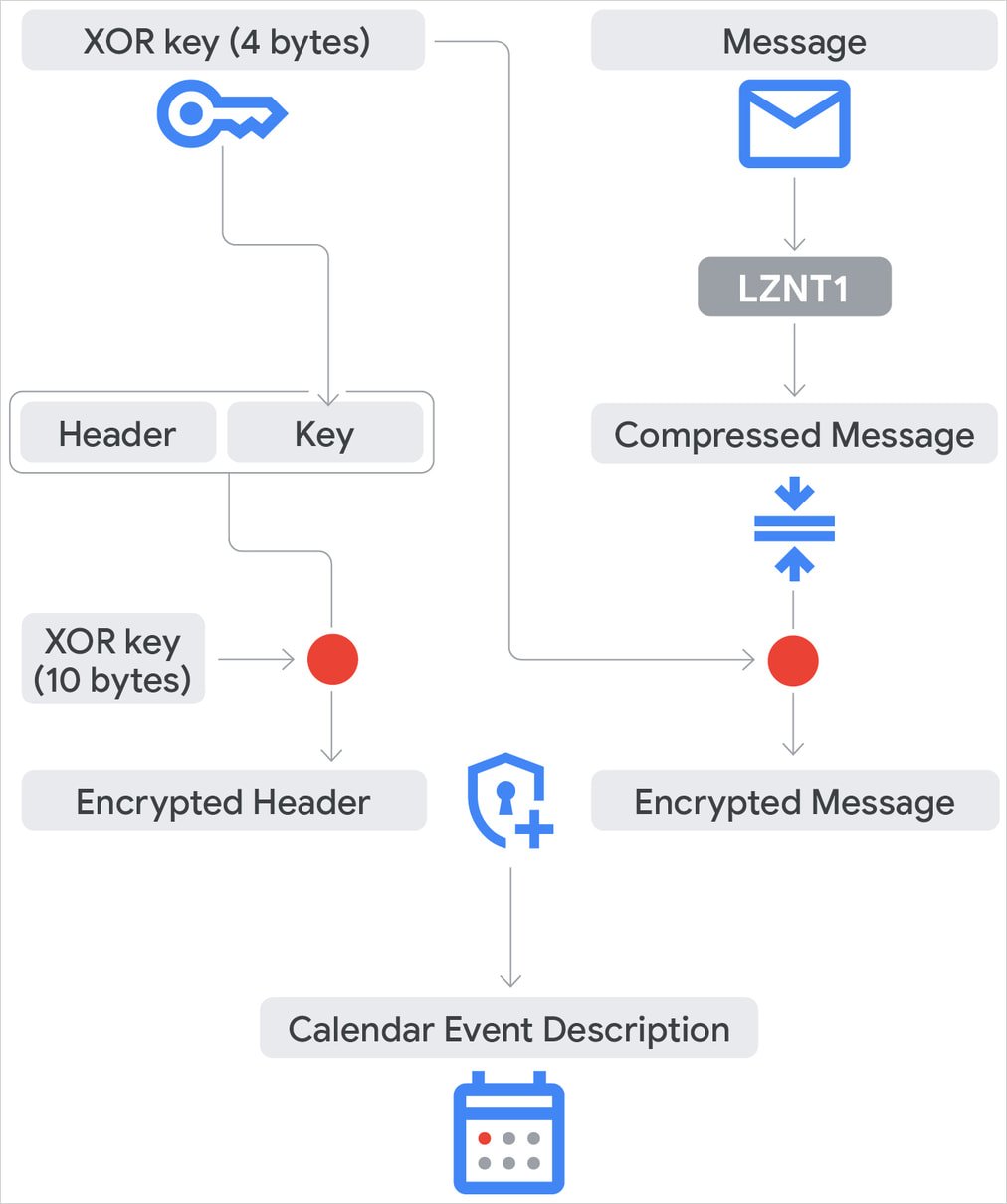
Source: Google
The useful charges never touching the disc and the C2 communication which takes place on a legitimate cloud service, the chances of being reported by the safety products on the infected host are minimal.
Disrupt the activity
Google has identified the Google calendar bodies controlled by the attacker and dismissed all related workspace accounts and incriminated calendar events.
Google’s safe navigation blocks has also been updated accordingly, so that users get a warning when visiting the associated sites, and traffic in these sites will be blocked on all products from the technology giant.
The report does not appoint specific organizations or compromises victims, but Google says that it has informed them directly in collaboration with Mandiant. Google also shared hard drilling samples and traffic newspapers with victims to help them identify infections in their environment.



